Implementations of WPA2 4-Way Handshake
What is a Supplicant?
From https://en.wikipedia.org/wiki/Supplicant_(computer):
In computer networking, a supplicant is an entity at one end of a
point-to-point LAN segment that seeks to be authenticated by an
authenticator attached to the other end of that link. The IEEE 802.1X
standard uses the term “supplicant” to refer either to hardware or
to software. In practice, a supplicant is a software application
installed on an end-user’s computer. The user invokes the supplicant
and submits credentials to connect the computer to a secure network.
If the authentication succeeds, the authenticator typically allows the
computer to connect to the network.
WPA_Supplicant is one implementation of software that performs this task. It is commonly used by the Open Source platforms, e.g. Linux, BSD, and Android.
What does installing a key mean?
Installing a key, whether it’s the PTK (Pairwise Transient Key) or the GTK (Group Temporal Key) involves a round trip through into the OS kernel, into the driver for your Wireless card and eventually to your wireless hardware itself.
The wireless card doesn’t know or care about the 4-way handshake, the WPA Supplicant handles those details. Thus, the keys are in multiple places in memory, one for each of these rings, i.e. userland, kernel, and hardware.
WPA_supplicant can only wipe its own copies of the keys, not those held in the wireless driver or chipset.
See https://w1.fi/cgit/hostap/tree/src/drivers/driver_nl80211.c#n2815 and https://www.kernel.org/doc/html/v4.12/driver-api/80211/cfg80211.html for details of the driver interface.
Image Author: Jordan Pryde
High-level diagram of WPA_Supplicant
There is a lot more to a complete WPA supplicant then just the 4-way handshake. For example, EAP is used to authenticate a user and agree on keying material without sharing a single master key. This is how eduroam and any enterprise Wi-Fi network works.
Appreciate the complexity by looking at this high-level diagram of WPA_Supplicant’s design.
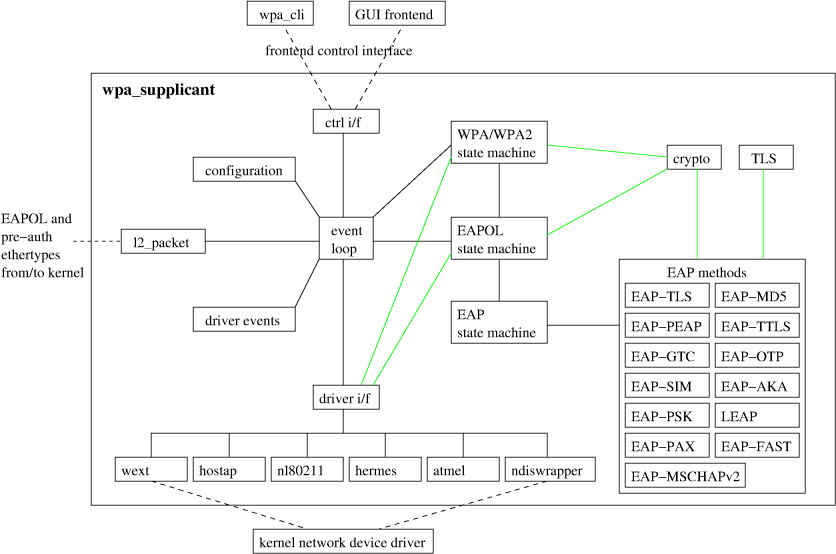
Image Source: https://w1.fi/wpa_supplicant/devel/
Fixes for KRACK
The WPA_supplicant KRACK fixes can be found at https://w1.fi/security/2017-1/.
In particular the fix for not installing an all-zero key is very simple. The below is an abridged version of the patch. We simply do not reinstall the key.
@@ -701,7 +700,7 @@ static int wpa_supplicant_install_ptk(struct wpa_sm *sm,
enum wpa_alg alg;
const u8 *key_rsc;
- if (!sm->tk_to_set) {
+ if (sm->ptk.installed) {
wpa_dbg(sm->ctx->msg_ctx, MSG_DEBUG,
"WPA: Do not re-install same PTK to the driver");
return 0;
Sources
- Key installation (driver): https://w1.fi/cgit/hostap/tree/src/drivers/driver_nl80211.c#n2815
- Key Installation (handshake): https://w1.fi/cgit/hostap/tree/src/rsn_supp/wpa.c#n698
- WPA 4-way handshake implementation documentation: https://w1.fi/wpa_supplicant/devel/wpa_8c.html
- wpa_supplicant docs: https://w1.fi/wpa_supplicant/devel/
- KRACK Patches: https://w1.fi/security/2017-1/
- cfg80211 Linux Kernel Subsystem: https://www.kernel.org/doc/html/v4.12/driver-api/80211/cfg80211.html